IP PBX security - Xorcom security best practices
IP PBX best practices, how to secure your IP PBX explained by Xorcom, IP PBX business phone systems developer, 2022 Get an IP PBX QuoteAll Xorcom Products
VoIP Telephony Fraud and how to keep your IP PBX Protected
The article for VoIP PBX system administrators.
In 2022 Telephony fraud is as high as ever, with estimated many billions of dollars annually in damages. VoIP PBX hacking has a significant share of the total numbers of telephony fraud, with hackers illegally using vulnerable PBX systems to sell minutes to customers and other illegal exploitations of such systems.
The damage of such a hack may easily reach tens of thousands of dollars per Telephony system over a single weekend and may also result in the leaking of company-confidential information.
While such attacks are extremely common and may cause significant damage, using best practices can reduce the risk of such an event to almost zero.
Among such IP PBX security best practices (the following refers to Xorcom CompletePBX IP-PBX):
- Firewall – make sure the CompletePBX system is located behind a properly set firewall, or use the internal CompletePBX firewall (for stand-alone CompletePBX systems).
- Passwords –
- by default, CompletePBX will offer strong passwords for devices and not allow weak passwords even when created manually. While this policy can be overridden in stand-alone CompletePBX systems it is highly recommended not to change this default.
- Change the default root password of the system
- Whenever the is a doubt – change passwords
- Use up-to-date software – under the service agreement, CompletePBX systems are eligible for software updates, including operating system updates. Make sure to update the system at least twice a year, or specifically on important security updates to ensure up to date and secure system. To make sure all your systems are covered under the service agreement contact us.
- SSH (Secure Shell Protocol) – when connecting to the PBX remotely always use secure communications. If possible:
- Allow SSH access only from specific IP addresses
- Deny root login from SSH
- PBX Web interface –
- limit access to the web interface as much as possible and refrain from using standard ports.
- Enable HTTPS in the CompletePBX configuration.
- SIP device setup – when possible, always limit the device to connect only from specific IP addresses (use Deny/Permit fields)
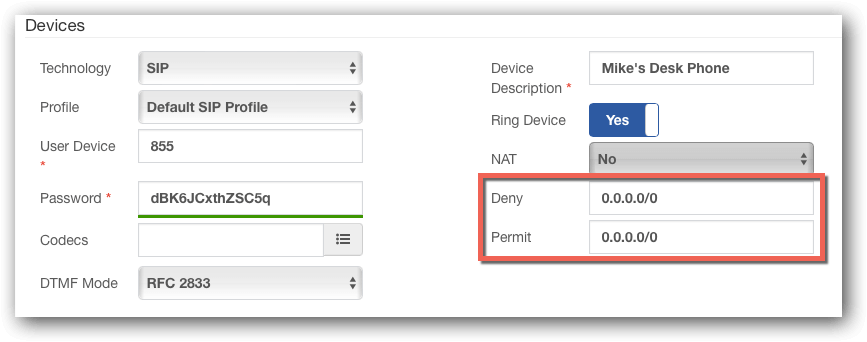
- Users – make sure inactive PBX users, such as former employees, are not left on the system.
- The organization’s internal procedures should ensure deleting such users (both extensions and administrative users) as soon as they are not longer in use.
- It is recommended to inspect the PBX system twice a year and verify that it is properly configured.
- Intrusion prevention – activated by default on all stand-alone CompletePBX systems (MT Manager uses a different SIP filtering mechanism). It is recommended not to change the default settings.
- Minimize potential damage – there are several things to be done in order to limit or even eliminate the potential damage even in cases where an unwarranted person (either from within the organization or from external hackers):

- Limiting permissions:
- Administrative users should have access to the features they need to administer only. This is set up in User Profiles.
- Limit allowed call destinations – most organizations work in limited geographies. International destinations that are known to be irrelevant to the organization should be disallowed for dialing by all users. It is also recommended to allow international dialing (when needed) only to relevant users.
- Limit call times – it is possible to limit certain types of destinations to only working hours.
Most hacking takes place at after hours, weekends and holidays. - Protect international dialing by a passcode – it is highly recommended to require the user to dial a passcode for each international call. The passcode can be user-based.
This setting alone can fully prevent toll fraud, even in the case, a hacker is in the system.
- System backups – make sure to have regular system backups in case you need to recover the PBX. Such backups can be done in several ways:
- All CompletePBX systems – via the Backup and Restore Module. This task can also be scheduled via the Task Manager to occur regularly.
- Enterprise appliances – Rapid Recovery USB full system backup.
- Virtual machines, multi-tenant platform – snapshots.
IP PBX tutorial - understanding the place of IP Telephony in the Network - explanatory video
In below video we explain the place of IP telephony in the network: All VoIP PBX videosFeel free to complete Xorcom online IP PBX Training course with a certificate.
Any questions related to IP PBX system security?
Get a free consultation from our expert via the form below.Latest Xorcom IP PBX Technical Updates
New CompletePBX Release – 5.2.12
In this version: Improved validation on time condition, bug fixes, and more…
New CompletePBX Release – 5.2.11
In this version: Improvements in caller ID modifications, voicemail behavior and features, phonebooks, queue agent options, and more..
How to Generate System Diagnostics File in Xorcom CompletePBX
In this release: caller ID prefixes for specific call types, hiding extensions from phonebook, phone provisioning, quick hotdesking login and more.
New CompletePBX Release – 5.2.10
In this release: caller ID prefixes for specific call types, hiding extensions from phonebook, phone provisioning, quick hotdesking login and more.
New CompletePBX Release – 5.2.9
In this release: User permissions in StatExplorer, additional improvements in StatExplorer and Switchboard. Diagnostic mode for troubleshooting, additional improvements, and bug fixes.
CloudPhone 1.0.21 – App Software Updates
CloudPhone iOS App Improved Spanish, Vietnamese and Chinese translations CloudPhone Android App Fixed app freezing on the incoming push call Fixed crash on Nubia device Fixed crash after provisioning Fixed long call audio setup delay on incoming calls Fixed Call...
